Dr. Michael L. Thomas
USAF Cyber College
mlt222@psu.edu
Abstract. Networks map and measure complex, and sometimes covert, human groups and organizations. The structure of their extended network begins to emerge as data is discovered via surveillance. A suspect being monitored may have many contacts — both accidental and intentional. We must always be wary of “guilt by association”. Accidental contacts, like the mail delivery person and neighbor must be eliminated as being worth with investigative interest. Intentional contacts are the persons of interest in the “underground economy”, such as a late afternoon visitor, whose car tag is traced back to a rental company at the airport, where we discover he arrived from Toronto and his name matches a cell phone number with a Buffalo, NY area code, that our person of interest calls regularly. This intentional contact is added to our map and we start tracking his interactions — where do they lead? As data comes in, a picture of the terrorist organization slowly comes into focus. Of equal value, is the idea that once a complicated network has been mapped, what gaps may exist as expressed in the visualization? Gaps where connections might exist can be identified and used as a means of “connecting the dots” with unknown persons of interest. Investigators are never sure they have uncovered enough information while they are in the process of uncloaking the underground organization. They have to contend with superfluous data. Some data is gathered after an event, so the investigators may know exactly what to look for. Before an event it is not so easy.
The November 2015, Paris attacks were a series of coordinated terrorist attacks that took place on 13 November 2015, in Paris, France and the city’s northern suburb, Saint-Denis. Beginning at 21:16 CET, three suicide bombers struck outside the Stade de France in Saint-Denis, during a football match. This was followed by several mass shootings and a suicide bombing, at cafés and restaurants. Gunmen carried out another mass shooting and took hostages at an Eagles of Death Metal concert in the Bataclan theatre, leading to a stand-off with police. The attackers were shot or blew themselves up when police raided the theatre. On the morning of 22 March 2016, three coordinated suicide bombings occurred in Belgium: two at Brussels Airport in Zaventem, and one at Maalbeek metro station in central Brussels. Thirty-two civilians and three perpetrators were killed, and more than 300 people were injured. Another bomb was found during a search of the airport. The Islamic State of Iraq and the Levant (ISIL) claimed responsibility for the attacks. The perpetrators seemed connected to the same terrorist cell which had been involved in the November 2015 Paris attacks. The NY Times published a series of visualizations showing the connections between various individuals in both groups but concrete evidence of collaboration between the groups couldn’t be found. Social Networking Analysis (SNA) provided an architecture and visualization that provided more detail that in fact there were plausible theories as to the nature of the connections that eventually led to the discovery of additional actors.
The data sources were publicly released information reported in major newspapers such as the New York Times, the Wall Street Journal, the Washington Post, and the Los Angeles Times among others including European News sources. As time progressed it became obvious and apparent that the investigators would not be releasing all the pertinent network/relationship information and actually might not have all the pertinent data. Initial conclusion – the data was not going to be as complete and accurate as needed for mapping and measuring organizational networks.
Three excellent papers recommended by Valdis Krebs form a working foundation for the knowledge needed to pursue this project.
- Malcolm Sparrow (Sparrow 1991) provides an excellent overview of the application of social network analysis to criminal activity. He describes three issues of criminal network analysis that are soon encountered in this process for this domain. a. Incompleteness – the inevitability of missing nodes and links that researchers and investigators will not uncover. b. Fuzzy boundaries – the issues in choosing who to include and not to include. c. Dynamic – the networks are not static. They change constantly. Rather than looking at the presence or absence of ties between two individuals, Sparrow suggests looking at the waxing and waning strength (measurable) of a tie depending upon the time and the task at hand.
- Wayne Baker and Robert Faulkner (Baker and Faulkner 1993) recommend reviewing all archival data to derive relationships. The data they accessed to analyze illegal price-fixing networks were mostly court documents such as sworn testimony. The data included accounts of observed (which led to inferred hypotheses of relationships) interpersonal relationships from various witnesses to these interactions. The attackers in Paris and Brussels were not directly observed by witnesses in great detail.
- Bonnie Erickson (Erickson 1981) documents the importance of trusted prior contacts for the effective functioning of a secret organization. The terrorists all appeared to have come from a network that had become organized while they were completing terrorist training in Syria. Many were familiar with each other by knowing each other in neighborhoods in Paris and Brussels for years. Some had lived together for prolonged periods. Some were related to each other. Deep trusted ties (strong ties), not easily discernable visible to outsiders, held this terror network together
Gathering the Data
Shortly after the attacks, information from investigators started to find its way to public sources in the media. The New York Times published a series of visualizations in 2016 (Buchanan & Haeyoun), (Parlapiano, et al) (Yourish et al) and soon the identities of multiple actors in the network became apparent. Facts available identified attackers, which attackers struck which targets, “support personnel” and which passports they had used to enter Europe either as permanent residents, citizens or refugees (Bronstein et.al.). Some had grown up in France or Belgium. As more information came into the open, data was also collected from European media sources about the attackers past. Beginning with the NY Times series of visualizations, Social Network Analysis (SNA) software was applied to the multiple data sources in order to provide a consolidated version of the links existing between the actors.
Several initial working hypotheses emerged as the visualizations were generated.
Hyp 1: Since many of the attackers and support personnel were of Moroccan descent, there must be some established link between the Kingdom of Morocco and the radicalization of the attackers.
Hyp 2: Since many of the attackers or support personnel had served prison time for various offenses, there must be some established link between the criminal elements in France and Belgium.
Hyp 3: All or some had visited or had attempted to visit Syria. Radicalization could have taken place within the Caliphate of ISIS.
After further examination of the visualizations provided by SNA, clear links between all of the dyads of the network could not be clearly established. Missing data would provide clarity provided it could be obtained.
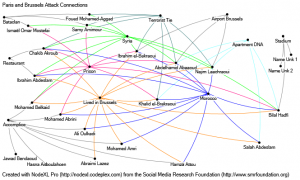
Figure 1. Initial sociograph combining hypothesized connections (links) based assumptions of time served in prison (purple), resident in Brussels (orange) or travel to or from Syria (green). Originally published on Twitter in late March 2016, these hypothesized links were dismissed as more data became revealed. This effectively eliminated Hyp 1 & 2 from further consideration. Original graphic by Dr. Michael L. Thomas.
As of 28March 2020, European authorities were still rolling up the network and following leads. Lack of cooperation between countries was hampering the sharing of intelligence and was proving to work in the favor if the terrorist network. “European authorities said they suspect that several men detained in a number of countries over the Easter weekend all had connections to perpetrators of the deadly attacks. This has prompted French and Belgian prosecutors to seek closer U.S. assistance, according to Western officials, as they try to map the extent of the network responsible for killing 130 people in Paris in November and at least 31 in Brussels on Tuesday.” (Gautier-Villers, et. al.)
On 28March, EU authorities requested intelligence assistance from the US.
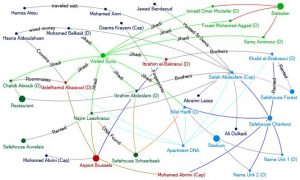
Figure 2. Refined SNA based on NY Times articles and originally published on Twitter on 29Mar2016. Hypothesis 3 (Syria) has been identified as the most viable construct. Included in the diagram are locations in France and Belgium that add geospatial context. Attack sites and locations where DNA evidence linked attackers are typical of the physical locations. The question in Hypothesis 3 is now refined to – who is acting as “control” guiding attackers from Syria and through EU checkpoints? This graph was widely distributed to both international LEAs and the IC. Original graphic by Dr. Michael L. Thomas.
As the investigation progressed, further information about the two unknown attackers began to emerge. They had been part of a team of 4 refugees detained enroute to Europe traveling from Syria. From further investigation, the names of the two attackers became known, the two teammates who were detained were released but re-arrested in Austria and further investigated. One of the 4 carried a mobile phone that contained contacts already in Europe – some of which were later identified as attackers in Paris and Brussels (Bronstein et. al). The 4 left crossed the border from Syria to Turkey in October of 2015 and headed for the Turkish coast when they departed for Greece. The 4 were initially detained in Greece where two were allowed to proceed onto Paris where they became the unidentified stadium bombers.

Figure 3. *The two men entered Europe via Greece in October – evidently by presenting themselves as Syrian migrants. The first pictured man had been carrying a passport that identified him as Ahmad al-Mohammad, from Idlib, Syria, but the French authorities say the passport may have been stolen. (Parlapiano et. al) At this time the two unknown attackers seemed to have little in common with the other attackers. They were part of a team of at least 4 identified in Greece.
Documents obtained by CNN and reported in Sept 2016 (Bronstein et. al) revealed details about the trip through Turkey, the subsequent boat journey to Greece and the interception by Greek authorities of all 4 (A Ahmad al-Mohammad, B Mohamad al-Mahmod, C Adel Haddadi & D Muhammad Usman) travelers. They all posed as Syrian refugees, blending in with the thousands fleeing Syria, and made their way from Izmir, Turkey, into Greece in a boat filled with dozens of refugees. The two who would bomb the stadium Paris (A & B) stadium were allowed to pass through Greece and started moving through Europe toward their target in France. While the two stadium bombers managed to pass through Greece, Greek authorities discovered the other two (C & D) were using fake Syrian passports. They were arrested, their money confiscated, and they were held for nearly a month.
Examination of one of the detained ISIS cellphones (Haddadi’s) revealed ISIS contacts in Germany, France, Belgium, Italy, Austria, Greece, Kuwait, Argentina, Algeria, Turkey, Spain, Pakistan, the Netherlands, and Morocco. The Greeks released the two detained agents in late October. They immediately contacted their ISIS handler, “Abu Ahmad”, who arranged to wire them 2,000 euros.
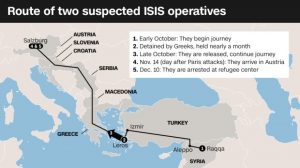
Figure 4. Refugee route through Europe from Syria taken by the 4 ISIS operators. (Graphic from CNN, Bronstein)
The remaining pair (C & D) continued along the refugee route. They were later (10Dec) detained again in Austria where upon interrogation revealed they had been intended to take part in the Paris bombings by Abu Ahmed. (Paravicini). Oussama Atar, now identified by Belgian authorities as “Abu Ahmad” was identified via a laptop computer disposed of in a garbage dump according to his arrest warrant. Two of his cousins had been the al-Bakraoui brothers who were identified as key members in the network after they participated in the Paris attacks.
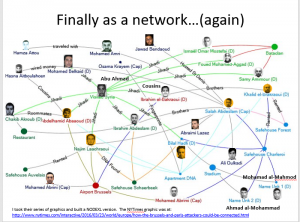
Figure 5. BBC reports Abu Ahmad (Oussama Atar) as the person acting as “control” ferrying ISIS agents into and out of the EU. On further exam, it was also reported he was a cousin of the Brussels airport bombers. His existence and significance had been hypothesized and reported 7 months earlier using SNA techniques. Original graphic by Dr. Michael L. Thomas.
Timeline of events:
2013-2015 – Abu Ahmad and Muhammed Abaooud make multiple trips between EU and Syria.
15Aug2015 – French authorities aware a concert hall attack is being planned.
Oct 2015 – 4 suspects detained in Greece. 2 released (they will later bomb the stadium in Paris) and 2 detained (will later be arrested in Austria) because of using forged Syrian passports.
13Nov2015 – Paris attacked in multiple locations by multiple teams.
10Dec2015 – Additional two suspects (C & D) from Greece detention arrested and interrogated in Austria. Later extradited to France.
22Mar2016 – Brussels airport attacked.
23Mar2016 – NY Times initial visualizations without SNA published.
28Mar2016 – EU authorities request US assistance in mapping terrorist network.
29Mar2016 – SNA performed using NodeXL Pro. Hypothesis of “control”/”handler” exists and is accepted because of gaps in visualization. Published on Twitter under “mthomas304”.
9Apr2016 – NY Times publishes updated visualization derived without using SNA techniques.
8Nov2016 – BBC identifies “Atar” as handler and coordinator of attacks.
2Jun2017 – BBC reports Belgium indicts and issues international warrant for “Atar” i.e. Abu Ahmad.
7Nov2018 – Brussels Times reports Abu Ahmad killed in Syria.
Conclusion – from the request for US assistance to the publication of Abu Ahmad in the open media and the subsequent international warrant, almost 7 months passed. Visualization of his existence using SNA made Europe less safe for him to operate in and facilitated the hasty retreat back to the ISIS Caliphate in Syria where he was later eliminated.
As the network structure emerged, a key dynamic that needs to be closely monitored is the activity within the network. Network activity spikes when a planned event approaches. Is there an increase of flow across known links? Are new links rapidly emerging between known nodes? Are money flows suddenly going in the opposite direction? When activity reaches a certain pattern and threshold, it is time to stop monitoring the network, and time to start removing nodes.
It has been hypothesized that a bottom-up approach of uncloaking a network is more effective than a top down search for the terrorist needle in the public haystack — and is less invasive of the general population, resulting in far fewer “false positives”.
All data for this analysis is ‘open source’ and was gathered from public sources on the WWW in Mar-Apr 2016. This white paper was written under the assumption that all surveillance data is gathered via legal means and that it will stand up in a court of law.
Broadcast Monday September 5, 2016
Bibliography
Baker, W.E. and R.R. Faulkner. 1993. The social organization of conspiracy: Illegal networks in the heavy electrical equipment industry. American Sociological Review 58(6) 837-860.
BBC (8Nov2016) Belgian jihadist Atar ‘coordinated’ Paris and Brussels attacks. https://www.bbc.com/news/world-europe-37906961 Accessed 24Aug2020.
BBC (2Jun2017) Belgium formally charges man in connection with Paris attacks. https://www.bbc.com/news/world-europe-40133105 Accessed 24Aug2020.
Bronstein, Scott; Gaouette, Nicole; Koran, Laura and Ward, Clarissa. (5Sep2016). First on CNN: ISIS planned for more operatives, targets during Paris attacks. https://www.cnn.com/2016/09/05/politics/isis-suspects-terrorism-europe-documents/. Accessed on 24Aug2020.
Buchanan, Larry & Park Haeyoun. (9Apr2016). Uncovering the Links Between the Brussels and Paris Attackers https://www.nytimes.com/interactive/2016/03/23/world/europe/how-the-brussels-and-paris-attackers-could-be-onnected.html?mtrref=undefined&assetType=PAYWALL Accessed on 24Aug2020.
Erickson, B.H. 1981. Secret societies and social structure. Social Forces 60(1): 188-210.
Gautier-Villers, David; Pop, Valentina; and Legorano, Giovani. (28Mar2016). Terror Network’s Web Sprawls Beyond Brussels and Paris. https://www.wsj.com/articles/terror-networks-web-sprawls-beyond-brussels-and-paris-1459124085 . Accessed 24aug2020.
Keller, Josh; Haeyoun, Park; White, Jeremy. Nov 2015. How the Organizer of the Paris Attacks
Slipped Through Authorities’ Hands. https://www.nytimes.com/interactive/2015/11/30/world/europe/paris-attacks-organizer-evaded-authorities.html. Accessed 24Aug2020.
Paravicini, Giulia, (22Mar2017). Paris and Brussels plotter who got away. https://www.politico.eu/article/paris-and-brussels-isis-terror-attack-plotter-who-got-away/ Accessed 24Aug2020.
Parlapiano, Alicia; Andrews, Wilson; Park, Haeyoun; Buchanan, Larry and Almukhtar, Sarah.2016. Unraveling the Connections Among the Paris Attackers. New York Times https://www.nytimes.com/interactive/2015/11/15/world/europe/manhunt-for-paris-attackers.html Accessed 24Aug2020.
Schneider, Oscar. (7November2018). Oussama Atar mastermind behind Paris and Brussels attacks killed in Syria. https://www.brusselstimes.com/brussels/51710/oussama-atar-mastermind-of-paris-and-brussels-attacks-killed-in-syria/ Accessed 24Aug2020.
Sparrow, M.K. 1991.The application of network analysis to criminal intelligence: An assessment of the prospects. Social Networks 13: 251-274..
Yourish, Karen: Watkins, Derek; White, Jeremy; Wallace, Tim; Smith, Patrick; Park, Haeyoun; Keller, Josh; Buchanan, Larry; Almukhtar, Sarah and Aisch, Gregor. (22Mar2016). What Happened at Each Location in the Brussels Attacks. https://www.nytimes.com/interactive/2016/03/22/world/europe/brussels-attacks-graphic.html. Accessed 24Aug2020.
Absolutely indited articles, Really enjoyed examining.
You could definitely see your enthusiasm in the work you write. The world hopes for even more passionate writers like you who aren’t afraid to say how they believe. Always follow your heart.