CellHawk helps law enforcement visualize large quantities of information collected by cellular towers and providers.
January 28, 2021
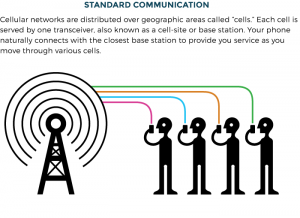
Cell phones are ubiquitous. As of 2021, there were more cell phones than people in the United States. Nearly 70 percent of those were smartphones, with 94 percent of millennials carrying a smart device. Cell phones go nearly everywhere, and users are increasingly dependent on smartphone applications for daily activities, such as texting, email, and location-assisted direction services.
Cellular technology also allows service providers to collect a wealth of information about a user’s whereabouts. Cellular service providers automatically record the location of cell phones at regular intervals, transforming them into personal tracking devices. One court described them as the “easiest means to gather the most comprehensive data about a person’s public — and private — movements.” Cell phone location data is collected in such high volume that it offers a nearly inexhaustible source of granular information, including when and where someone goes, with whom, and even for what purpose.
A cell phone’s location information can be collected in several ways. First, a cell phone accesses its network through signals transmitted by cell towers. The cell phone searches for the strongest signal and continually connects to a cell tower as the user moves within the network, whether or not a call is underway. When it connects to a cell tower, the phone transmits identifying information to the service provider. This enables the provider to “track the phone, discontinue service, or blacklist it from a network.” The density and proliferation of cell towers make it increasingly possible to lo-cate an individual phone to within a few feet of its position.
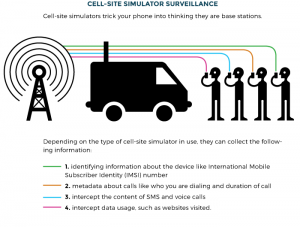
Cell site simulators can be used in two ways. First, if an officer already knows the location of a phone down to the radius of several blocks or a neighborhood, he or she can drive around the area with the simulator to pinpoint the precise location.26 As part of this process, the cell site simulator will “also intercept the data of other cell phones in the area, including the phones of people not being investigated.” Second, the device can be used to identify all the cell phones (and, by extension, their subscriber information) at a given location, such as a protest. Cell site simulators are generally used in such a way that “[t]he phone’s user will not know” they are being tracked, so law enforcement can use the tool for location surveillance without the public’s knowledge. As of November 2020, the U.S. Departments of Justice, Homeland Security, and Treasury owned numerous cell site simulators, as did 75 law enforcement agencies in 27 states and the District of Columbia.

Stingray II cell phone tower simulator. Screenshot: Michael Thomas
Smartphone location data can also be obtained through the phone’s use of Wi-Fi, Bluetooth, and GPS. Smartphones continuously send out signals containing identifying information to establish connections with these technologies; in the case of GPS, smartphones receive signals from GPS satellites and perform calculations based on the timing and other features of the signals to determine their location — indeed, a phone can calculate its GPS location, even with no WiFi or cellular connection, because it does not need to broadcast anything to receive the GPS signals. Smartphones store their location history until the user takes affirmative steps to clear the data. Third-party applications running on smartphones can also request and receive geolocation data without any direct action on the part of the user. Law enforcement can request this data directly from these third-party providers like Google and Facebook, often with delayed notice to users.
Generally, there are two types of device used by law enforcement that are often referred to interchangeably: passive devices (which we will call IMSI catchers), and active devices (which we will call cell-site simulators.) Passive devices, as a rule, do not transmit any signals. They work by plucking cellular transmissions out of the air, the same way an FM radio works. They then decode (and sometimes decrypt) those signals to find the IMSI of the mobile device and track it.
Screenshot: Michael Thomas
It is difficult for most people to know whether or not their phone’s signals have been accessed by an active cell-site simulator, and it is impossible for anyone to know if their phone’s signals have been accessed by a passive IMSI catcher. Apps for identifying the use of cell-site simulators, such as SnoopSnitch, may not be verifiably accurate. Some more advanced tools have been built, which may be more accurate. Some are exceedingly more accurate such as Cellhawk.
Until now, the Bartonville, Texas, company Hawk Analytics and its product CellHawk have largely escaped public scrutiny. CellHawk has been in wide use by law enforcement, helping police departments, the FBI, and private investigators around the United States convert information collected by cellular providers into maps of people’s locations, movements, and relationships. Police records obtained by The Intercept reveal a troublingly powerful surveillance tool operated in obscurity, with scant oversight.
CellHawk’s maker says it can process a year’s worth of cellphone records in 20 minutes, automating a process that used to require painstaking work by investigators, including hand-drawn paper plots. The web-based product can ingest call detail records, or CDRs, which track cellular contact between devices on behalf of mobile service providers, showing who is talking to whom. It can also handle cellular location records, created when phones connect to various towers as their owners move around.
Such data can include “tower dumps,” which list all the phones that connected to a given tower — a form of dragnet surveillance. The FBI obtained over 150,000 phone numbers from a single tower dump undertaken in 2010 to try and collect evidence against a bank robbery suspect, according to a report from the Brennan Center for Justice at NYU.
CellHawk’s surveillance capabilities go beyond analyzing metadata from cellphone towers. Hawk Analytics claims it can churn out incredibly revealing intelligence from large datasets like ride-hailing records and GPS — information commonly generated by the average American. According to the company’s website, CellHawk uses GPS records in its “unique animation analysis tool,” which, according to company promotional materials, plots a target’s calls and locations over time. “Watch data come to life as it moves around town or the entire county,” the site states.
The tool can also help map interpersonal connections, with an ability to animate more than 20 phones at once and “see how they move relative to each other,” according to a promotional brochure.
CellHawk helps police exploit information already collected by private telecommunications providers.
The company has touted features that make CellHawk sound more like a tool for automated, continuous surveillance than for just processing the occasional spreadsheet from a cellular company. CellHawk’s website touts the ability to send email and text alerts “to surveillance teams” when a target moves, or enters or exits a particular “location or Geozone (e.g. your entire county border).”
On its website, Hawk Analytics claims this capability can help investigators “view plots & maps of the cell towers used most frequently at the beginning and end of each day.” But in brochures sent to potential clients, it was much more blunt, claiming that CellHawk can help “find out where your suspect sleeps at night.”

A screenshot showing the previously more honest version of their marketing. Screenshot: Michael Thomas
Data Sharing and Loose Regulation in Minnesota
The sheriff’s office in Hennepin County, Minnesota, which includes Minneapolis, certainly seemed impressed after it started using the software in early 2015. One criminal intelligence analyst lauded CellHawk’s ease of use in a February 2016 email comparing the subscription software to a competing tool. “CellHawk is pretty new and a lot cheaper! The great thing about cellhawk is that it is ‘hands off’ by the user, as the software does everything for you. It is drag and drop. The software can download calls from all major phone companies. The biggest selling point is of course the mapping. it also has animation, which is cool!”
Hennepin County Sheriff’s Office uses CellHawk as part of an effort to share intelligence through a Minnesota fusion center known as the Metro Regional Information Center, which brings together the FBI and eight counties serving up to 4 million people, according to the St. Cloud Times. In February 2018, the latest year for which The Intercept obtained HCSO invoices, the sheriff’s office renewed its annual subscription, providing the capability to store 250,000 CDRs.
A spokesperson for the sheriff’s office, Andrew Skoogman, said the office used certain CellHawk features infrequently. For example, it is “extremely rare” for HCSO to analyze tower dumps, he said, and “fairly rare” for it to use CellHawk’s automated location alerting service, which is used “based in the analytical needs of the investigator.”
The telecommunications data at the heart of CellHawk is shared extensively by providers. For example, Verizon in 2019 received more than 260,000 subpoenas, orders, warrants, and emergency requests from various U.S. law enforcement entities, including more than 24,000 for location information. But the legal requirements for obtaining that information are sometimes unclear. The American Civil Liberties Union in 2014 called the legal standards related to tower dumps “extremely murky.” A 2018 Brennan Center report stated that the courts were “split” on the handling of such dumps, with some lower courts allowing access to the data using a court order, which under the Stored Communications Act is obtained using a lower evidentiary standard than a warrant, requiring only “reasonable grounds to believe” the records are relevant to an ongoing investigation. Location records particular to a given subscriber, meanwhile, can be obtained with just a court order — unless they span seven days or more, in which case police need to get a full warrant, according to a 2018 Supreme Court ruling. Courts have also been divided on whether police need a court order or warrant to obtain “real-time” cellular location data.
Screenshot: Michael Thomas
Hennepin County defined its own legal standards to rely upon in deploying technology like CellHawk. These were articulated in a sheriff’s office policy document dated August 2015 — months after CellHawk was already in use. The document, titled “Criminal Information Sharing and Analysis,” was released following a data request that was initiated in 2018 and fulfilled several years later following the election of a new sheriff. It stated that the office needed “[r]easonable suspicion,” which was deemed “present when sufficient facts are established to give … a basis to believe that there is, or has been, a reasonable possibility that an individual or organization is involved in a definable criminal activity or enterprise.”
The policy does not say that investigators must receive approval from a judge to retain information. Skoogman did not respond to The Intercept’s question about what legal standard is applied to the collection of CDRs.
Chad Marlow, senior advocacy and policy counsel for the ACLU, when asked to review Hennepin County’s CellHawk policy, said the CellHawk technology was “not inherently problematic” but that the county set a low standard for how it handles the collection of CellHawk data. Requiring “reasonable suspicion” is a typical threshold for traffic stops, not for intrusive searches, which require probable cause. CellHawk’s capabilities — combing through data from calls, texts, ride-hailing applications, etc. — are patently more intrusive than a traffic stop. Beyond that, Marlow said, the county’s “definition of reasonable suspicion is bizarrely convoluted” and should require that investigators “have to have a reasonable basis for a crime being committed not MAY BE being committed.”
Hennepin County’s policy continued:
Criminal intelligence information shall be retained for up to five years from the date of collection of use, whichever is later. After that time, this information shall be deleted unless new information revalidates ongoing criminal activities of that individual and/or organization. When updated criminal intelligence information is added into the file on a suspect individual or organization, such entries revalidate the reasonable suspicion and reset the five year standard for retention of that file.
The policy empowers HCSO investigators to scoop up this data and retain it for five years based on a fairly low legal standard.
And while this policy says the sheriff may not retain information based “solely” on support for “unpopular causes” or an individual’s “race, gender, age or ethnic background” and “personal habits and/or predilections that do not break any laws or threaten the safety of others” — mentioning activities covered by the First Amendment — if a crime were to occur during a protest, as is routine, that data is considered fair game by law enforcement. Under such low standards and with such a powerful surveillance utility, it wouldn’t take long to map out the social network of an entire protest movement.
Under such low standards and with such a powerful surveillance utility, it wouldn’t take long to map out the social network of an entire protest movement.
For instance, during a protest outside a detention center in downtown Minneapolis to show solidarity with demonstrations in neighboring Wisconsin following the shooting of an unarmed Black man by the Kenosha Police Department, Dave Hutchinson, the Hennepin County sheriff, said, “11 individuals were arrested and are being held on probable cause riot, damage to property and unlawful assembly,” according to an HCSO press release. Should the criminal intelligence investigators at the fusion center run those individuals’ information through CellHawk, it is not at all a stretch to say that the police would then possess a map of those individuals’ associations based on calls, texts, and other records. That map of social interactions could include thousands of activists who were not at all party to the crimes of which those 11 individuals are accused. Hawk Analytics markets such social network analysis as a primary feature.
When asked whether the use of CellHawk undermined the presumption of innocence — essentially reversing the investigative process, so that evidence comes first and suspicion of a specific crime after — Skoogman replied, essentially, that innocent people had nothing to fear. “People come under suspicion of having committed a crime based on information developed by investigators,” he wrote. “Based on evidence developed by those investigations, a suspect’s cell phone records may be obtained and analyzed. On occasion, that analysis has developed information suggesting that the suspect did not commit the crime under investigation. This is the investigative process. It is exactly why data is analyzed. To determine whether the data available supports continued focus on an individual as a suspect or perhaps rules them out.”
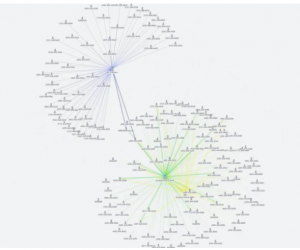
Screenshot from a Hawk Analytics promotional video displaying “link analysis,” which reveals a large network of “co-conspirators and associates” in a matter of seconds. The more data points, in this case cellphone numbers, run through CellHawk likely exponentially expands the number of other individuals roped into an investigation. Screenshot by Michael Thomas.
Deployed — and Promoted — Across the Country
Hawk Analytics CEO Mike Melson, whose bio on the company website describes him as a former NASA engineer, offers free trials to law enforcement organizations to which he hopes to sell his product. Additionally, Melson has worked as an expert witness, ready to testify on behalf of prosecutors. His testimony sometimes appears in local news outlets without mention of the fact that he is the CEO of the company that could stand to financially benefit, albeit indirectly, from a conviction. Hawk Analytics failed to comment on the record after multiple attempts were made over the phone and by email.
“This highlights how the rapid development of surveillance tech outstrips existing laws.”
In December 2013, Heather Elvis went missing from her South Carolina home after becoming embroiled in a lovers’ quarrel. Several years later, an 11-day trial resulted in two 30-year sentences for one Tammy Moorer. During the second day of that trial, Melson made an appearance as “an expert witness when it comes to analyzing cell phone data,” according to WBTW News 13. The station did not include that Melson was intimately involved in the creation of software that helped connect the dots in this case.
Additionally, according to reports from Northern Virginia, Hawk Analytics was reimbursed for their expert services which led to “the prosecution of a man convicted of first-degree murder in the 2017 shooting death of a … CVS store manager.” For their “cellular data analysis and two days of expert testimony,” Hawk Analytics was paid $8,175. That certainly isn’t a windfall, but it rivals the amount made from the sale of a small number of CellHawk subscriptions, and it effectively compounds revenue streams from multiple sides of the criminal justice system.
CellHawk is not the only technology that investigators in the Twin Cities use to process intelligence about suspects and others. Hennepin County and their law enforcement partners use automated license plate readers; stingrays and competing, similar devices; aerial surveillance; and social media intelligence, among other spy tech. CellHawk alone is powerful — but added to the area police’s already expansive arsenal, it tips local law enforcement toward becoming more like intelligence agencies than municipal cops.
Lengthy data retention policies and the power of these surveillance tools create a litany of frightening possibilities for overreach and abuse. While HCSO has acknowledged its use of some of these tools, it has not released any public reports on its use of CellHawk. Rachel Levinson-Waldman, deputy director of the Brennan Center’s liberty and national security program, who reviewed Hennepin County’s policy said, “The reference to use is concerning, since that could significantly expand the time for retention.”
Minnesota state law requires an individual whose electronic device was subject to a tracking warrant be notified within 90 days if that evidence did not end up in court. This “tracking warrant” law has been on the books since 2014 and yet, judging from press reports in recent years, it’s not clear anyone in the state has ever received such a notice or if a tracking warrant has ever been unsealed by the courts. The law seems to have been thwarted in part by police avoiding warrants and obtaining instead court orders under the much lower “reasonable suspicion” standard. This, despite the fact that Minnesota law clearly states, under a subdivision titled “Tracking warrant required for location information,” that “a warrant granting access to location information must be issued only if the government entity shows that there is probable cause the person who possesses an electronic device or is using a unique identifier is committing, has committed, or is about to commit a crime.”
Julia Decker, policy director for the ACLU of Minnesota, said that “there doesn’t seem to be oversight” for the use of CellHawk in the state, even though surveillance should get oversight of “the highest standard possible.” She also said that Hennepin’s policy to retain CellHawk and similar data for five years raises the potential for harm to civil liberties.
“I think this highlights how the rapid development of surveillance tech outstrips existing laws, and how that can be really problematic,” said Decker. “Without oversight/regulation, powerful surveillance technology is integrated into already-existing investigatory frameworks, instead of being examined and considered beforehand for its potential to actually expand or push the limits/bounds of those frameworks and encroach on civil liberties. … In this moment of talking about police reform, use of surveillance tech needs to be part of the discussion.”
Hawk Analytics has many clients around the United States. This reporter conducted a survey using the Freedom of Information Act to collect invoices for CellHawk subscriptions from agencies referenced on CellHawk’s website, referred to in CellHawk’s training sessions, or mentioned in local news reports. He found numerous agencies fielding the technology: Atlanta and Fayette County, Ga.; Kansas City, Kan.; Franklin County, Va.; Utah County, Utah,; Fort Collins, Colo.; Hidalgo County, Texas; Orange County, Calif.; and, of course, the FBI all have paid for CellHawk in the last several years. The Madison, Wisconsin, police department appears to have thousands of potential CellHawk records from 2018 alone but has demanded close to $700 to examine and provide them.
Recently events have conflated to provide an insight to the use of this technology paired with others. Specifically, these events are the take-down of the Parler website combined with the use of the data when used in examining the presence of Parler users during the Jan 6, 2021, riot at the US Capitol. At least several users of the far-right social network Parler appear to be among the horde of rioters that managed to penetrate deep inside the U.S. Capitol building and into areas normally restricted to the public, according to GPS metadata linked to videos posted to the platform the day of the insurrection in Washington.
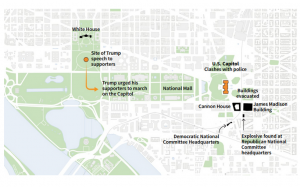
Overview of Capitol area and events of Jan 6, 2021. Screenshot by Michael Thomas.
The data, obtained by a computer hacker through legal means ahead of Parler’s shutdown, offers a bird’s eye view of its users swarming the Capitol grounds after receiving encouragement from President Trump — and during a violent breach that sent lawmakers and Capitol Hill visitors scrambling amid gunshots and calls for their death. GPS coordinates taken from 618 Parler videos analyzed by Gizmodo has already been sought after by FBI as part of a sweeping nationwide search for potential suspects, many of whom are already in custody.
The siege on January 6, which lasted approximately two hours, resulted in five deaths, including that of a Capitol police officer whom authorities say was bludgeoned with a fire extinguisher and later succumbed to his injuries. Windows were smashed, tables overturned, and graffiti scrawled and scratched into the walls of the 220-year-old building—some calling for the murders of journalists sheltering in place nearby.

Cell phone locations inside a bounding box containing the US Capitol. Graphic: Dhruv Mehrota / Gizmodo, Screenshot by Michael Thomas.
The siege on January 6, which lasted approximately two hours, resulted in five deaths, including that of a Capitol police officer whom authorities say was bludgeoned with a fire extinguisher and later succumbed to his injuries. Windows were smashed, tables overturned, and graffiti scrawled and scratched into the walls of the 220-year-old building—some calling for the murders of journalists sheltering in place nearby.
Gizmodo mapped nearly 70,000 geo-located Parler posts and isolated hundreds published on January 6, near the Capitol where a mob of pro-Trump supporters had hoped to overturn a democratic election and keep their president in power. The data shows Parler users posting all throughout the day, documenting their march from the National Mall to Capitol Hill where the violent insurrection ensued.
The precise locations of Parler users inside the building can be difficult to place. The coordinates do not reveal which floors they are on, for instance. Moreover, the data only includes Parler users who posted videos taken on January 6. And the coordinates themselves are only accurate up to an approximate distance of 12 yards (11 meters).
The red dot just south of the Capitol Rotunda’s center on the map above is linked to a video Gizmodo verified that shows rioters in red MAGA hats shouting obscenities about House Speaker Nancy Pelosi, whose office is a short walk to the west. But other dots nearby could indicate videos captured in adjacent offices, stairwells, or hallways leading toward the House and Senate chambers. A second video successfully linked to the Parler data belongs to a rioter who filmed a mob in the Rotunda chanting, “Whose House? Our House?” (while facing the Senate side of the building).
Other coordinates pulled from Parler point to users roaming the north side of the building near the Senate chamber, either near leadership offices or the press gallery, depending on which floor they were on.
Moments before the siege, Vice President Mike Pence was presiding over a debate to certify the vote entangled by the baseless allegations of election fraud endorsed by his Republican colleagues. Reporters observed from the gallery. Sen. Ted Cruz, who had for weeks amplified false claims of a stolen election, was seemingly oblivious to the violence outside as he stood to argue against certifying Arizona’s electoral votes.
Other location data from outside the Capitol follows the precise route the crowd took from the National Mall shortly after a speech by President Trump, in which he urged his supporters to “fight like hell,” saying they could not “take back [their] country with weakness.”
The FBI declined to provide any specifics about the materials it is collecting as part of its ongoing investigation. Investigators did, however, seek access to the Parler GPS data on Monday, according to a source with knowledge of the effort.
The Parler data was first obtained by a hacker identified by her Twitter handle, @donk_enby, as reported by Gizmodo on Monday.
In an interview Monday, @donk_enby said she began to archive posts from Parler the day of the siege, documenting what she described as “very incriminating” evidence linked to a mob of Parler users on the Hill. When it later became clear that Amazon intended to expel the app from its servers, she expanded her efforts to vacuum up the entirety of its content.
According to @donk_enby, more than 99% of all Parler posts, including millions of videos bearing the locations of users, were saved. Unlike most of its competitors, Parler apparently had no mechanism in place to strip sensitive metadata from its users’ videos prior to posting them online.
Authorities have launched sprawling investigations across the country to locate suspects who took part in the siege, including a man photographed in a grey hoodie suspected of placing explosive devices outside the offices of the Republican and Democratic National Committees. Among the 20 arrests so far, a Colorado man who allegedly brought guns and hundreds of rounds of ammunition with him to Washington, saying he wanted to murder Pelosi.
Two Capitol police officers were suspended on Monday, including one who took selfies with rioters inside the Capitol building and another who reportedly donned a MAGA hat while directing them around the building.
The Parler data is currently downloadable from https://tracker.archiveteam.org/parler/#show-all. Questions remain unanswered.
- Were USSOCOM air assets used in the NCR during this interlude to collect cell phone data? There seemed to be such an assets in use earlier in the year over Portland, Oregon following protests there by the BLM movement.
- What tools were used to merge the cellphone data with the Parler users and by whom? This is not a trivial task. Parsing the Parler data from specific users is one of the steps in such a task, but matching users from the Parler data with users present at the Capitol implies many were already likely under surveillance.
- Under what authorities were/are USSOCOM air assets used in CONUS?
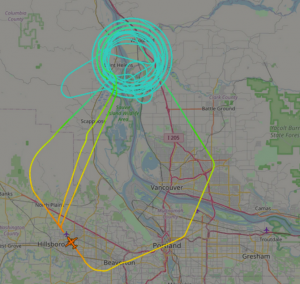
Flight data from a recent SIGIINT collection AC, the DO-328 “Cougar” mission just outside Portland. Screenshot by Michael Thomas.
A full briefing of ISR test assets is provided in the “Sources” re “Forsyth”.
Sources
Biddle, Sam, July 23, 2020, “An Air Force Special Operations Surveillance Plane Is Lurking Near Portland During Federal Crackdown,” accessed 28Jan2021 from https://theintercept.com/2020/07/23/air-force-surveillance-plane-portland-protests/
Brewster, Thomas, Jan14, 2021, “The FBI Investigated Parler User’s Call For Proud Boys To Violently Attack Government Officials—Three Weeks Before The Capitol Hill Siege,” accessed 28Jan2021 from https://www.forbes.com/sites/thomasbrewster/2021/01/14/weeks-before-the-siege-the-fbi-was-investigating-parler-users-call-for-proud-boys-violence-on-capitol-hill/?sh=1d8aa7056a0c
Cameron, Dell, Jan11, 2021, “Every Deleted Parler Post, Many With Users’ Location Data, Has Been Archived,” accessed 28Jan2021 from https://gizmodo.com/every-deleted-parler-post-many-with-users-location-dat-1846032466
Cameron, Dell and Mehrotra, Dhruv Jan 12, 2021, “Parler Users Breached Deep Inside U.S. Capitol Building, GPS Data Shows,” accessed 28Jan2021 from https://gizmodo.com/parler-users-breached-deep-inside-u-s-capitol-building-1846042905
Deutsche Aircraft Press Release, Dec 15, 2020, “Deutsche Aircraft to shape the future of aviation as D328eco™ aircraft accelerates transition to zero emissions aircraft,”, accessed 28Jan2021 from https://www.prnewswire.com/news-releases/deutsche-aircraft-to-shape-the-future-of-aviation-as-d328eco-aircraft-accelerates-transition-to-zero-emissions-aircraft-301193198.html
Electronic Frontiers Foundation Website, (no date), “Cell-Site Simulators/IMSI Catchers,” accessed 28Jan2021 from https://www.eff.org/pages/cell-site-simulatorsimsi-catchers
Fang, Lee, Jun 24, 2020, “FBI Expands Ability to Collect Cellphone Location Data, Monitor Social Media, Recent Contracts Show, Recent contracts with Dataminr and Venntel show a growing focus on harnessing the latest private sector tools for mass surveillance.” accessed 28Jan2021 from https://theintercept.com/2020/06/24/fbi-surveillance-social-media-cellphone-dataminr-venntel/
Forsyth, Col Eric, (no date2015 – Tampa), “Special Operations Forces Industry Conference, Breakout Session”, accessed 28Jan2021 from https://ndiastorage.blob.core.usgovcloudapi.net/ndia/2015/SOFIC/PEOFWForsyth.pdf
Forsyth, Col Eric, (no date 2016 – Tampa), “Special Operations Forces Industry Conference, Portfolio Review”, accessed 28Jan2021 from https://ndiastorage.blob.core.usgovcloudapi.net/ndia/2016/SOFIC/PEOFWForsyth.pdf
Levinson-Waldman, Rachel, (no date), “Cellphones, Law Enforcement, and the Right to Privacy, HOW THE GOVERNMENT IS COLLECTING AND USING YOUR LOCATION DATA,” accessed 28Jan2021 from https://www.brennancenter.org/sites/default/files/2019-08/Report_Cell_Surveillance_Privacy.pdf
War is Boring Press Release August 17, 2015, “Meet the U.S. Air Force’s Commando Test Plane,” accessed 28Jan2021 from https://warisboring.com/meet-the-u-s-air-forces-commando-test-plane/
Zetter, Kim, July 31 2020, “How Cops Can Secretly Track Your Phone,” accessed 28Jan2021 from
https://theintercept.com/2020/07/31/protests-surveillance-stingrays-dirtboxes-phone-tracking/
I enjoy what you guys tend to be up too. This sort of clever work and exposure! Keep up the very good works guys I’ve you guys to blogroll.
Very nice info and straight to the point. I don’t know if this is actually the best place to ask but do you people have any thoughts on where to employ some professional writers? Thank you 🙂
Can you elaborate a bit on the second topic you mentioned?
So this type of tech combined with cell metadata dumps will reveal to the FBI who was complicit in the storming of the Capitol.
Absolutely. Folks just don’t realize they can be tracked using cellphone.
I抦 not sure where you’re getting your information, but good topic. I needs to spend some time learning much more or understanding more. Thanks for great info I was looking for this info for my mission.
whoah this blog is magnificent i like studying your articles. Stay up the good work! You already know, lots of persons are searching round for this information, you could aid them greatly.
Hello there, I discovered your site by means of Google while searching for a related matter, your website came up, it appears to be like good. I have bookmarked it in my google bookmarks.
Thanks for another great post. Where else could anybody get that kind of information in such a perfect way of writing? I’ve a presentation next week, and I am on the look for such info.
There is clearly a bunch to identify about this. I feel you made some good points in features also.
An interesting discussion is worth comment. I think that you should write more on this topic, it might not be a taboo subject but generally people are not enough to speak on such topics. To the next. Cheers
Have you ever considered about adding a little bit more than just your articles? I mean, what you say is fundamental and everything. But just imagine if you added some great graphics or videos to give your posts more, “pop”! Your content is excellent but with images and videos, this blog could certainly be one of the very best in its niche. Very good blog!
Hey there I am so thrilled I found your website, I really found you by error, while I was searching on Google for something else, Anyways I am here now and would just like to say thanks a lot for a remarkable post and a all round enjoyable blog (I also love the theme/design), I don抰 have time to look over it all at the moment but I have saved it and also added your RSS feeds, so when I have time I will be back to read much more, Please do keep up the superb work.
I was just seeking this information for a while. After 6 hours of continuous Googleing, finally I got it in your site. I wonder what’s the lack of Google strategy that don’t rank this kind of informative web sites in top of the list. Usually the top web sites are full of garbage.
I enjoy, lead to I discovered exactly what I used to be having a look for. You have ended my four day long hunt! God Bless you man. Have a nice day. Bye
A lot of thanks for your whole hard work on this blog. Gloria really loves going through investigation and it is easy to see why. I notice all relating to the compelling form you deliver both interesting and useful tactics through this web blog and as well invigorate contribution from the others on that point then our favorite simple princess has been understanding a lot. Enjoy the rest of the new year. You’re the one carrying out a fantastic job.
Currently it looks like WordPress is the best blogging platform available right now. (from what I’ve read) Is that what you are using on your blog?
I like what you guys are up also. Such intelligent work and reporting! Keep up the superb works guys I have incorporated you guys to my blogroll. I think it’ll improve the value of my site 🙂
Good post. I learn something more difficult on totally different blogs everyday. It’s going to at all times be stimulating to learn content from other writers and follow a little one thing from their store. I抎 choose to use some with the content material on my blog whether you don抰 mind. Natually I抣l provide you with a link in your net blog. Thanks for sharing.
I loved as much as you will receive carried out right here. The sketch is attractive, your authored subject matter stylish. nonetheless, you command get got an nervousness over that you wish be delivering the following. unwell unquestionably come further formerly again as exactly the same nearly a lot often inside case you shield this hike.